The cyber threat landscape has changed dramatically by 2026. Traditional perimeter-based security models — where everything inside a network is trusted — no longer work. As businesses move deeper into cloud platforms, remote work, APIs, microservices, and AI-driven systems, attackers have more entry points than ever.
This is why Zero Trust Security has become the dominant cybersecurity framework.
And in 2026, AI is the engine that powers it.
Zero Trust operates under one simple rule:
“Never trust, always verify.”
No user, device, application, or API is trusted automatically — even if they are already inside the network.
AI enables Zero Trust to analyze identity, behavior, and risk continuously, making access decisions more accurate and secure. Let’s explore how this works and why 2026 is the year Zero Trust becomes fully AI-driven.
🔐 What Zero Trust Security Really Means in 2026
Many people think Zero Trust only means strict authentication, but in 2026 it includes:
-
Identity security
-
Device health verification
-
Continuous authentication
-
Real-time threat detection
-
Network micro-segmentation
-
AI-driven access decisions
-
API and cloud workload protection
In 2026, Zero Trust is no longer a manual framework; it’s powered by AI, automation, and predictive analytics.
🤖 How AI Powers Zero Trust Security in 2026
AI gives Zero Trust systems the ability to:
-
Learn user behavior
-
Understand device patterns
-
Identify anomalies
-
Detect insider threats
-
Spot compromised accounts
-
Analyze millions of access requests instantly
Traditional security tools look at simple yes/no authentication.
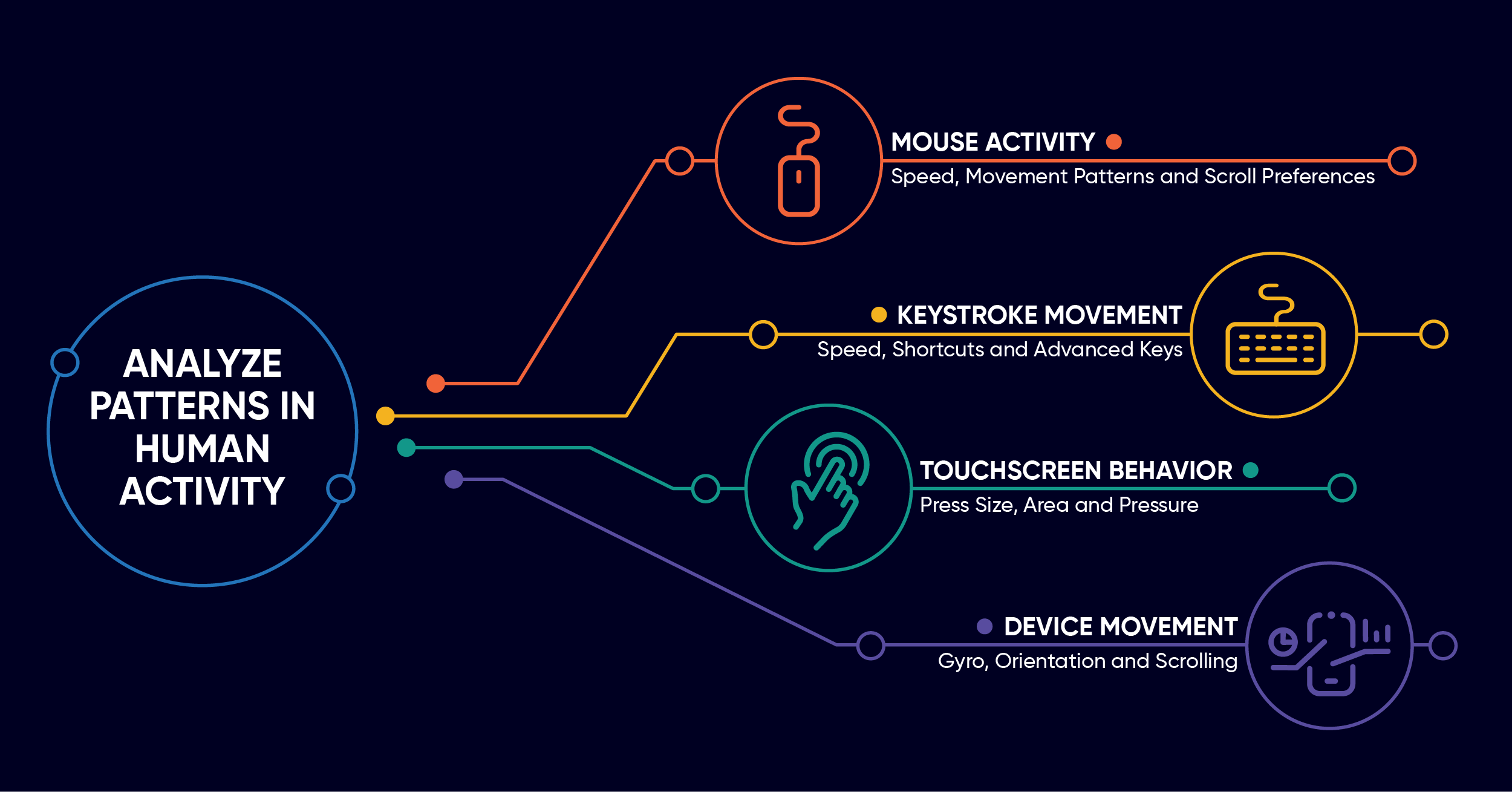
AI looks at context, such as:
-
Location
-
Device identity
-
Time of access
-
Past behavior
-
Access patterns
-
Typing speed (behavioral biometrics)
-
API request behavior
This transforms Zero Trust from a static model into a dynamic, adaptive one.
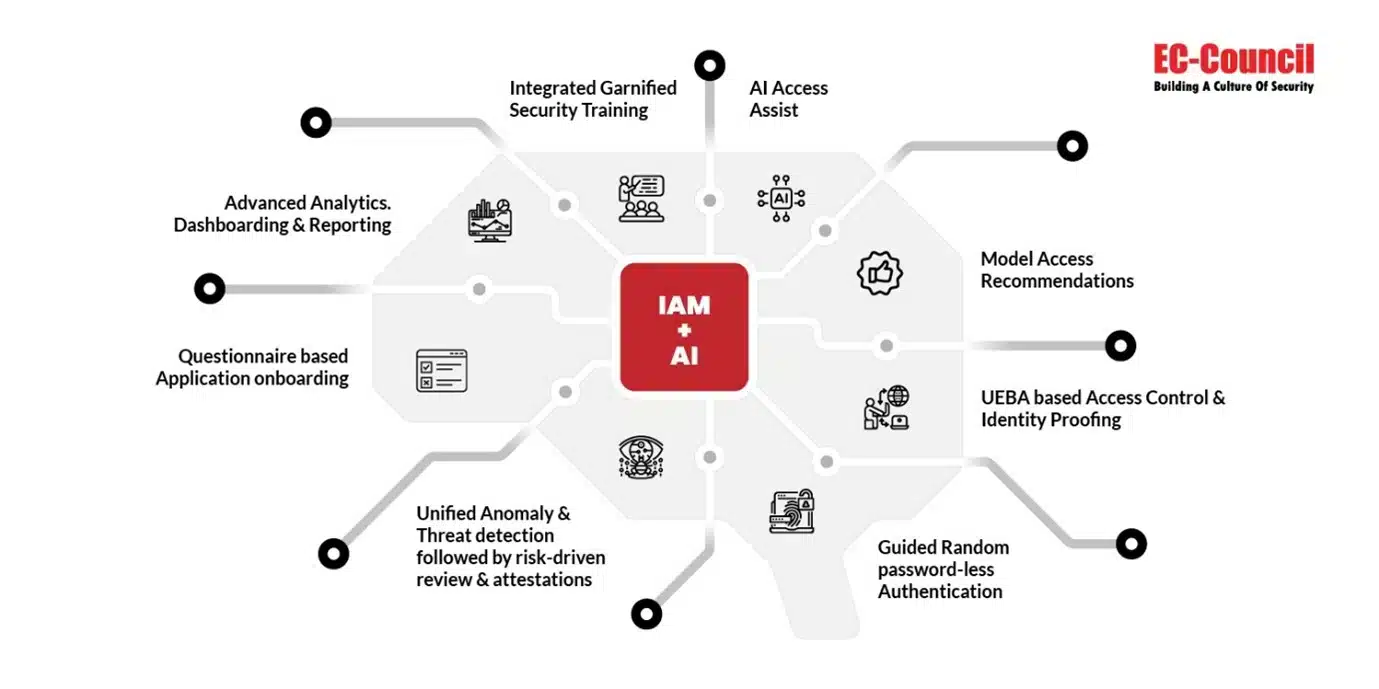
⚡ 1. AI for Identity & Access Management (IAM) in 2026
Identity is the foundation of Zero Trust.
In 2026, AI analyzes identity in real time by studying:
-
User location
-
Device fingerprint
-
Login history
-
Behavior patterns
-
Digital body language (typing speed, mouse movement)
-
Multi-factor authentication behavior
If anything looks abnormal, AI challenges the user or blocks access automatically.
AI helps with:
✔️ Stopping account takeovers
✔️ Detecting compromised sessions
✔️ Applying conditional access policies
✔️ Continuous verification instead of one-time login
Identity-based attacks were the most common breach in earlier years.
In 2026, AI dramatically reduces this risk.
💻 2. AI-Driven Device Security (Zero Trust for Endpoints)
Endpoints include:
-
Laptops
-
Mobile phones
-
IoT devices
-
Virtual machines
-
Cloud workloads
In 2026, AI monitors device health continuously:
-
Is the device updated?
-
Has malware been detected?
-
Is the device behaving differently than usual?
-
Is someone trying to escalate privileges?
If the device becomes risky, AI:
-
Blocks access
-
Limits privileges
-
Triggers remediation steps
Zero Trust means every device must prove it is safe at all times.
🌐 3. AI-Powered Network Micro-Segmentation
Traditional networks allowed free movement once inside the perimeter.
This is how ransomware attacks spread so quickly.
AI-powered Zero Trust in 2026 uses micro-segmentation, meaning:
-
Every network segment is isolated
-
Applications only access what they need
-
Workloads cannot freely communicate
-
Lateral movement is blocked
AI detects unusual movement inside a network, such as:
-
A server connecting to a new endpoint
-
A device trying to access unauthorized databases
-
Suspicious communication patterns
This stops attackers from moving deeper once they break in.
☁️ 4. Zero Trust Cloud Security Powered by AI
With hybrid and multi-cloud environments taking over in 2026, AI is essential for:
-
Monitoring cloud logs
-
Protecting APIs and microservices
-
Detecting configuration errors
-
Identifying unauthorized access
-
Managing identity permissions
Cloud security risks often come from misconfigurations.
AI identifies and fixes these issues automatically.
🔍 5. AI for Real-Time Threat Detection in Zero Trust
Zero Trust requires continuous monitoring, not one-time decisions.
AI constantly analyzes:
-
Access logs
-
Traffic flows
-
API requests
-
User behavior
-
Device activity
AI detects early signs of attacks, including:
-
Ransomware encryption
-
Phishing attempts
-
Insider threats
-
Privilege escalation
-
Malware activity
-
Data exfiltration
Every decision is based on risk, not assumptions.
You May Also Read : How AI Is Used in Cyber Defense: A Simple Guide for 2026
⚙️ 6. Automated Response: AI Makes Zero Trust Fast
In 2026, AI automates many defensive tasks:
-
Locking compromised accounts
-
Blocking malicious IPs
-
Isolating infected devices
-
Requiring step-up authentication
-
Applying risk-based access rules
AI reduces response time from hours to seconds.
This is crucial because modern cyberattacks happen extremely fast.
🛡️ 7. Zero Trust for APIs and Microservices (AI Secures the Modern Stack)
As APIs become the backbone of apps, AI secures them by:
-
Detecting abnormal API traffic
-
Monitoring bots
-
Identifying harmful requests
-
Checking authentication tokens
-
Preventing API abuse
AI is essential for protecting:
-
SaaS platforms
-
Mobile apps
-
AI models and AI agents
-
Cloud-native microservices
Zero Trust extends into every API connection and digital interaction.
🌟 Benefits of AI-Powered Zero Trust in 2026
✔️ Stronger protection against modern attacks
AI detects threats humans cannot.
✔️ Faster response times
Automated actions stop attacks immediately.
✔️ Reduced false positives
AI learns normal patterns over time.
✔️ Secures all environments
Cloud, on-prem, hybrid, IoT, and APIs.
✔️ Stops insider threats
Behavior-based detection identifies unusual actions.
✔️ Enables secure remote work
Zero Trust removes the need for traditional VPNs.
⚠️ Challenges of AI-Driven Zero Trust
Even though AI improves Zero Trust, challenges still exist:
-
Requires high-quality data
-
Attackers use AI too
-
Models must be updated
-
Skilled cybersecurity teams are needed
-
AI can make mistakes if misconfigured
Still, AI remains the strongest driving force behind modern Zero Trust adoption.
🔮 The Future of Zero Trust Beyond 2026
Here’s what’s coming next:
⭐ Autonomous cyber defense
AI will automatically detect, block, and fix threats.
⭐ AI-driven deception systems
Fake networks that trap attackers.
⭐ Quantum-resistant Zero Trust
Built to handle future quantum computing attacks.
⭐ AI-powered SOC copilots
Intelligent assistants supporting security teams.
⭐ Fully identity-driven networks
Every connection based on verified identity signals.
🏁 Conclusion
Zero Trust in 2026 is more than an access control model — it is a complete AI-powered security framework. With cyber threats growing more advanced and networks becoming more complex, Zero Trust provides the structure and AI delivers the intelligence.
Companies that adopt AI-driven Zero Trust security will be far more protected, more adaptive, and more resilient against modern cyberattacks.